Zero trust model
It assumes the worst case scenario. It therefore protects the resources also like that.
MS recomments the following Zero trust models:
- Verify explicitly: Always authenticate and authorized on all data points.
- Least privileged access: I should only pass really required permissions.
- Assume breach: Always assume that the network is already compromised.
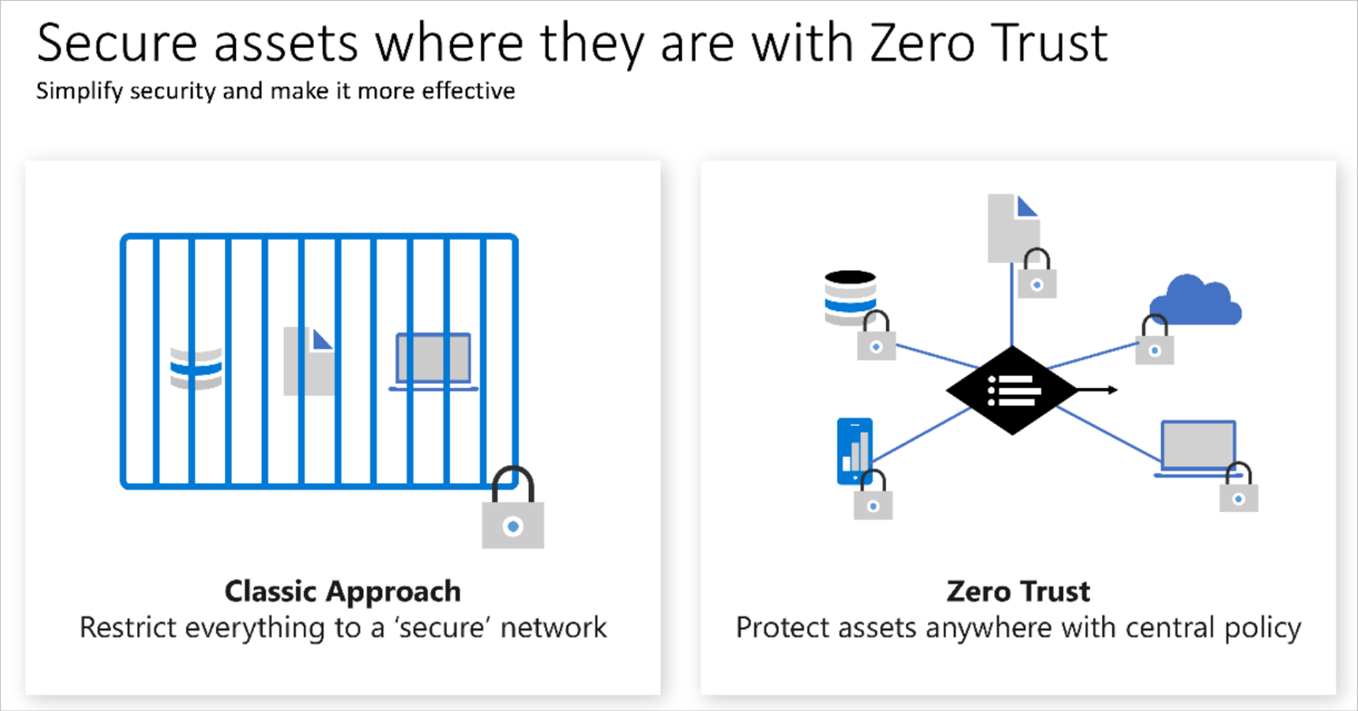
Adjusting to the Zero trust model
- Classic model: All devices are restricted to join the network. So for example, only cooperate devices are allowed. No personal devices are allowed and also I got tightly controlled VPN access.
- Zero trust model: It flips the logic. Here it does not assume a device is safe but it asks me to authenticate against it. So the location of the device is less of a matter but the authentication matters more
Graph from MS: